I’ve seen a bunch of attempts to hack at my zencart admin area and an old phpBB2 install that is no longer there. Both of these don’t work, and just return a 404 error, but it’s kind of annoying to keep spending compute cycles on this sort of behavior. Besides, now that I have installed the statsd and graphite packages, I am set up to provide a graph of whatever I want. So why not track the hackers, lock them out, and provide a graph of activity at the same time? So here goes.
2016-12-28 edit: see my github repo at https://github.com/dminear/apache_hack_check
I also run mod_perl in the Apache2 server, so I wanted to hook in to the PerlAccessHandler and do the work. The following is the Apache2 config lines:
PerlModule ModPerl::DanHandler <Location /> #SetHandler perl-script PerlAccessHandler ModPerl::DanHandler </Location>
And the following is the Perl module that is in the /usr/local/lib/site_perl/ModPerl directory on my Ubuntu machine:
package ModPerl::DanHandler;
use strict;
use warnings;
use FileHandle;
use IO::Socket::INET;
use Apache2::Log;
use Apache2::RequestRec ();
use Apache2::Connection ();
use Apache2::Const -compile => qw(FORBIDDEN OK :log);
BEGIN {
mkdir "/tmp/bad_ips";
chmod 0777, "/tmp/bad_ips"
}
my $sock = IO::Socket::INET->new(PeerPort => 8125,
PeerAddr => '127.0.0.1',
Proto => 'udp');
sub handler {
my $r = shift;
my $str = $r->connection->remote_ip();
# if there is an attempt to access "zencart/admin", then put the ip on the block list
if ($r->unparsed_uri() =~ /zencart\/admin$/ ||
$r->unparsed_uri() =~ /zencart\/+admin\/+/ ||
$r->unparsed_uri() =~ /phpbb2/i ) {
#$r->log_error("BAD IP: $str");
$sock->send( "hacker.unparsed_uri." . $r->unparsed_uri() . ":1|c\n" ) if defined $sock;
my $fh = FileHandle->new( "> /tmp/bad_ips/$str");
if (defined $fh) {
print $fh "dummy";
$fh->close;
}
}
# check the block list
if (-e "/tmp/bad_ips/$str") {
$sock->send( "request.blocked:1|c\n" ) if defined $sock;
return Apache2::Const::FORBIDDEN;
} else {
$sock->send( "request.allowed:1|c\n" ) if defined $sock;
$sock->send( "request.hostname." . $r->hostname() . ":1|c\n" ) if defined $sock;
return Apache2::Const::OK;
}
}
1;
So now when someone comes in and tries to access /zencart/admin (or some gyrations thereof), the IP address gets stored in the tmp directory as a filename. On every request, the remote IP address is checked, and if found returns a 403 Forbidden response. The nice thing is that this happens for any request thereafter. Because it’s early in the request stage, there’s not too much overhead. Plus I get the satisfaction of watching the banned IP addresses grow.
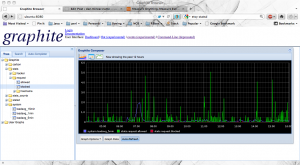
Then there’s some logic to update the statsd server based on good or bad requests. Here’s a screen capture of it in action (click on the image to enlarge):





 You can see the cut and capped off pipe in the second picture below. I was lucky to find the supply line was a 3/4 inch pipe, and then a 1/2 inch teed off and went back down. Since there was a 1/2 inch in the kitchen, then that was the one. I would have had to guess otherwise.
You can see the cut and capped off pipe in the second picture below. I was lucky to find the supply line was a 3/4 inch pipe, and then a 1/2 inch teed off and went back down. Since there was a 1/2 inch in the kitchen, then that was the one. I would have had to guess otherwise.
 The pipes on the left are cold water, and the hot water is on the right. There is a previous cap from an earlier slab leak a few years ago, so now both pipes are capped. My job is the left solder work, which I think is a better job!
The pipes on the left are cold water, and the hot water is on the right. There is a previous cap from an earlier slab leak a few years ago, so now both pipes are capped. My job is the left solder work, which I think is a better job!



 Well, I was up at 6:00am to meet Chris and Brian in Lake Forest at 7am. We started up via Maple Springs Road at 8am, and it was a nice drive. The road was in good condition, and I always forget how long the road goes until the
Well, I was up at 6:00am to meet Chris and Brian in Lake Forest at 7am. We started up via Maple Springs Road at 8am, and it was a nice drive. The road was in good condition, and I always forget how long the road goes until the  That was not the case on the ground. I thought that it would be too cold, but I was wrong. It was the busiest I have ever seen on Santiago, both with the bugs and people. I don’t know how many hikers, bikers, and joyriders there were. When I was up on the tower, a motorcycle rider came up, got off his bike, and asked for Dan. “What? Was that ITD?” Yup, it sure was. I have not seen Eric Robitaille for about 10 years! And now were talking on the top of Santiago. Weird. There was also a rescue going on to the north about 6 miles away on Skyline Road of a body in a car over the side. While that was going on, a guy rolls up in a pickup to the emergency crew saying he just got bit by a rattlesnake. There was a lot of coordination trying to figure out if they could helicopter the guy out. I never found out how things ended. When stuff happens, it happens.
That was not the case on the ground. I thought that it would be too cold, but I was wrong. It was the busiest I have ever seen on Santiago, both with the bugs and people. I don’t know how many hikers, bikers, and joyriders there were. When I was up on the tower, a motorcycle rider came up, got off his bike, and asked for Dan. “What? Was that ITD?” Yup, it sure was. I have not seen Eric Robitaille for about 10 years! And now were talking on the top of Santiago. Weird. There was also a rescue going on to the north about 6 miles away on Skyline Road of a body in a car over the side. While that was going on, a guy rolls up in a pickup to the emergency crew saying he just got bit by a rattlesnake. There was a lot of coordination trying to figure out if they could helicopter the guy out. I never found out how things ended. When stuff happens, it happens.